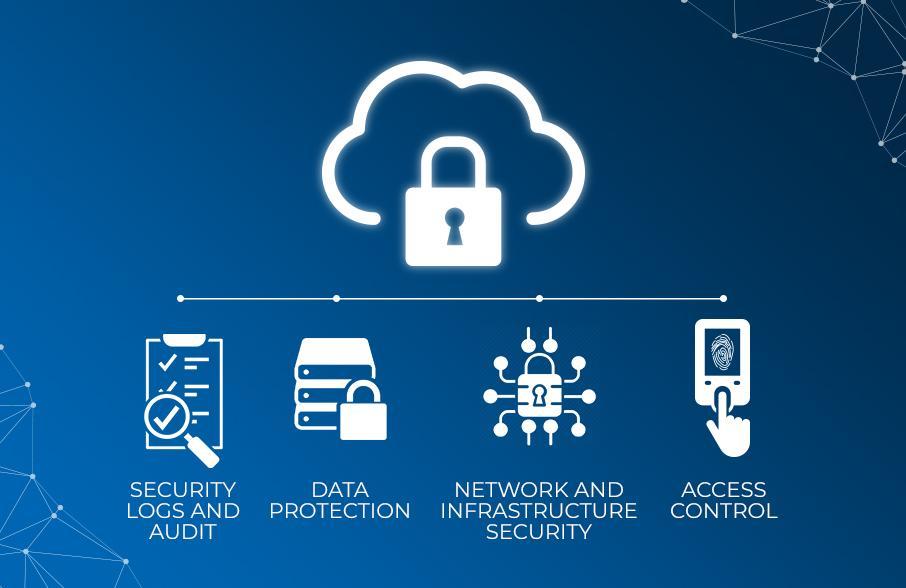
What are cloud security services?
Cloud Security Services Can be a set of control-based safeguards and technology protection designed to safeguard resources stored online from leakage, theft, or data loss. Security applications operate as software within the cloud employing a Software as a Service (SaaS) model.
What are the three sorts of cloud services?
Three main service models of cloud computing:-
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (SaaS).
How do I provide cloud security?
Here are some tips your business can use to confirm the safety of information in your cloud.
Ensure Local Backup it’s a vital precaution that one can take towards cloud data security.
- Avoid Storing Sensitive Information.
- Use Encryption.
- Apply Reliable Passwords.
- Additional Security Measures.
- Test Your Security.
- Also Read.
What are the advantages of cloud security?
5 Benefits of a Cloud Computing Security Solution:-
- Protection against DDoS:-
Due to a frequent number of attacks on Distributed denial of service, and a top cloud computing security solution focuses on measures to prevent huge amounts of traffic aimed toward a company’s cloud servers.
- Data security.
- Regulatory compliance.
- Flexibility.
- High availability and support.
What is the simplest cloud security certification?
(ISC)2 Certified Cloud Security Professional (CCSP) the foremost well-known and established cloud security certification is (ISC)2’s CCSP.
Difference Between Cloud and cloud security?
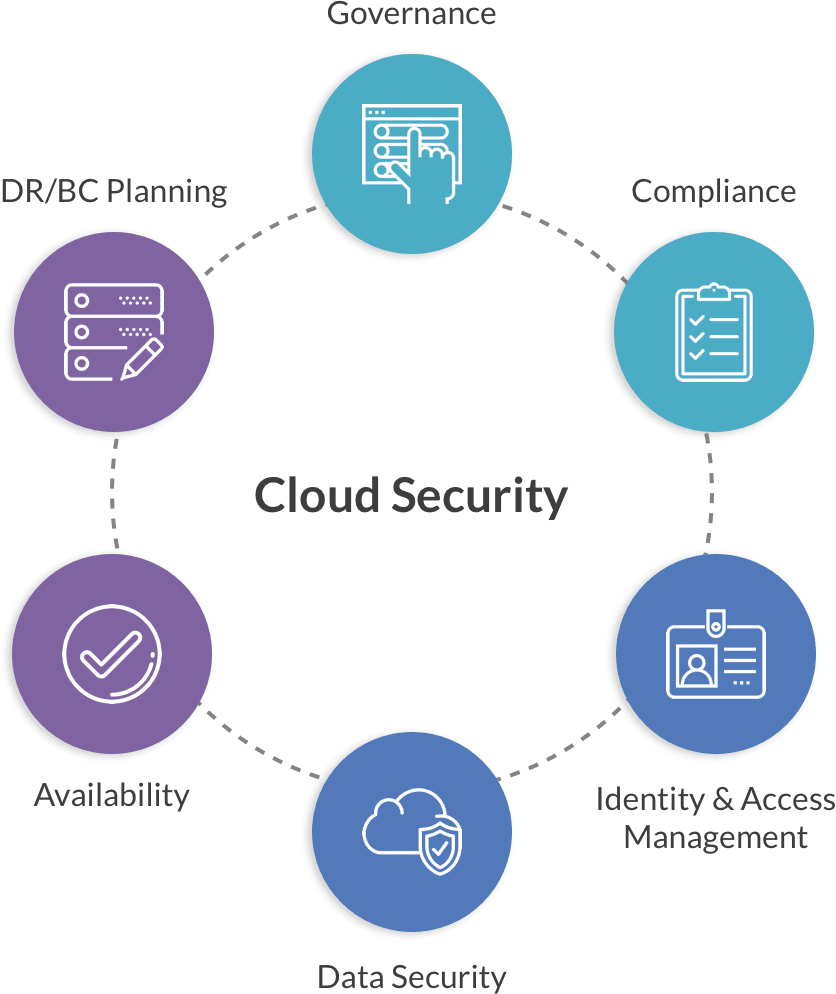
Cloud security, also called cloud computing security, consists of a collection of policies, controls, procedures, and technologies that employment together to guard cloud-based systems, data, and infrastructure. By verifying access to purify traffic, cloud security is configured to the precise needs of the business.
Why is Cloud Security So Important?
In the absence of securing the cloud, you’re risking all of the information you employ, and ultimately the integrity of your business. Why would a client still work with you after their data was stolen because of your lack of security?
There’s also the unfortunate statistic that 60% of breaches involve vulnerabilities that a patch is out there but not applied. you would like to possess a team constantly monitoring for potential security threats, and ensuring that your cloud infrastructure systems are always up-to-date.
Here are the 6 best ways you’ll be able to improve cloud security
Deploy Multi-Factor Authentication (MFA)
The traditional username and password combination is commonly insufficient to guard user accounts against hackers, and stolen credentials are one of the most ways hackers get access to your online business data and applications.
Once they need your user credentials, they will log into all those cloud-based applications and services that you simply use a day to run your business.
Manage Your User Access to enhance Cloud Computing Security
Allocating the access control not only helps prevent an employee from accidentally editing information that he or she isn’t authorized to access but also protects you from hackers who have stolen an employee’s credentials.
Real-time Monitoring, Logging in and Analyzing User Activities With Automated Solutions to Detect Intruders
Real-time monitoring and analysis of user activities can facilitate your spot irregularities that deviate from normal usage patterns, e.g., log in from a previously unknown IP or devices.
These abnormal activities could indicate a breach in your system so catching them too soon can stop hackers in their tracks and permit you to mend security issues before they cause mayhem.
There are many data protection solutions that will facilitate your out with this, starting with automated 24/7 networking monitoring and management and moving up to advanced cybersecurity solutions such as:-
- Intrusion Detection & Response
- Vulnerability Scanning and Remediation
- Endpoint Detection and Response
Every business has varying needs for various levels of cybersecurity services, so make sure to urge a 3rd party risk assessment before making any large investments.
Create a Comprehensive Off-boarding Process to shield against Departing Employees
When employees leave your company, ensure they’ll now not access your cloud storage, systems, data, customer information, and intellectual properties.
Since each employee would likely have access to several different cloud applications and platforms, you wish a systemized deprovisioning process to confirm that each one of the access rights for every departing employee is revoked.
Provide Anti-Phishing Training for workers on a Daily Basis
Hackers can gain access to secure information by stealing employees’ login credentials through social engineering techniques like phishing, spoofing websites, and social media spying.
For Example, the rapid expansion of Microsoft Office 365 has made it an awfully attractive target for hackers – more and more threats are emerging, specifically the frequency of phishing attacks.
Consider Cloud to Cloud Back-Up Solutions
There are legitimate risks related to any cloud application suite or platform.
As mentioned, the percentages of you losing data due to your cloud provider’s mistake is incredibly low – but losing that data thanks to human error is high.
If an employee should accidentally delete data, a hacker obtains an account password and corrupts the information, or a rogue employee cleans out his inbox and folders – there’s nothing Microsoft can do past a specific period.
Note:- That the majority of cloud providers, including Microsoft, do store deleted data in their data centers for a brief period of your time, including your Office 365 data.

But make sure to test along with your cloud provider to see what this point frame is, and if there are fees to revive that data (when possible to retrieve it.)
Companies that have to abide by strict regulations or are concerned with being held liable thanks to missing or corrupted data are turning to cloud-to-cloud backup solutions.